Requirements Management Cybersecurity Market Size and Trends
Cutoff in 2021, the global requirements management cybersecurity market was growing at a steady rate. According to a report by MarketsandMarkets, the market size was estimated to be USD 5.8 billion in 2020 and was expected to grow to USD 11.8 billion by 2025, at a Compound Annual Growth Rate (CAGR) of 15.3% during the forecast period.
The report cited several factors driving the growth of the requirements management cybersecurity market, including the increasing demand for security solutions due to the rising number of cyber-attacks, the growing adoption of cloud-based solutions, and the increasing use of the Internet of Things (IoT) and Bring Your Own Device (BYOD) policies. Additionally, the report noted that the increasing adoption of artificial intelligence (AI) and machine learning (ML) technologies for cybersecurity was also contributing to the growth of the market.
In terms of trends, the report highlighted that there was a growing focus on integrating cybersecurity requirements into the software development life cycle (SDLC) and the need for organizations to ensure compliance with industry standards and regulations. The report also noted that there was a trend towards the use of automated tools for requirements management and cybersecurity, as these tools could help organizations save time and reduce errors.
Electronics of Tomorrow
The Electronics of Tomorrow trade fair showcases the latest technologies and trends in the electronics industry, with a focus on embedded systems, software development, and cybersecurity. The event attracts exhibitors and attendees from around the world and provides an opportunity for industry professionals to network, exchange ideas, and learn about new products and technologies.

The trade fair typically features a variety of exhibits, seminars, and workshops covering topics such as the Internet of Things (IoT), artificial intelligence (AI), machine learning (ML), robotics, automation, and more. Additionally, the event offers opportunities for attendees to connect with experts in the field, attend product demonstrations, and participate in hands-on activities.
Visure Solutions at the EOT 2023, Denmark
With the rapid advancement of technology in industries, cybersecurity has become a crucial necessity to protect an organization’s assets from malicious attacks. In order to ensure compliance with industry standards and regulations while protecting against potential security vulnerabilities, requirements management is essential. This helps organizations save time and money while delivering secure and compliant software products.
Effective requirements management is critical for any organization seeking to ensure the security and compliance of its products or services. In the software requirement specifications, cybersecurity requirements should be integrated to address authentication, authorization, data integrity, and access control issues. By doing so, organizations can avoid costly mistakes resulting from a lack of attention to detail regarding security best practices.
Cybersecurity is a major concern for embedded systems, encompassing all of the technology and operations used to safeguard devices and their platforms and networks against cyberattacks or hacking. Development teams for embedded systems already know many concepts and techniques to mitigate security risks, such as coding rules, dedicated RTOS, cryptography techniques, static and dynamic analysis, and more. However, one aspect that is often overlooked is requirements management and traceability.
Even though security standards like IEC 62443 / ISA Secure require managing and tracing security requirements throughout the development and testing lifecycle, many engineers are unsure how to efficiently comply with these requirements and which types of checks and processes apply to requirements management.
Therefore, Micaël Martins, European Sales Leader at Visure, delivered a thorough presentation on “How to Write and Manage Requirements for Cybersecurity Embedded Projects” at the Electronics of Tomorrow 2023 in Denmark.
Why Requirements Management is so important in Embedded Safety and Security Standards
Requirements management is particularly important in the context of embedded safety and security standards due to the critical nature of the systems involved. Here’s why:
- Compliance with Standards: Embedded safety and security standards, such as ISO 26262 for automotive systems or IEC 61508 for industrial control systems, define rigorous requirements for ensuring the safety and security of these systems. Requirements management helps in capturing, documenting, and managing these standards-specific requirements, ensuring compliance throughout the development lifecycle.
- Risk Identification and Mitigation: Embedded safety and security standards require a thorough understanding of potential risks and their mitigation strategies. Requirements management helps identify and assess safety and security risks, allowing for the development of appropriate requirements to address these risks. It also enables traceability between risks, requirements, and the implemented solutions, ensuring that safety and security measures are adequately implemented.
- Traceability and Accountability: Safety-critical systems demand traceability and accountability for each requirement. Requirements management ensures that safety and security requirements are properly traced from their origins to the design, implementation, and testing stages. This traceability helps demonstrate compliance with standards, facilitates change management, and enables effective impact analysis when modifications or updates are required.
- Verification and Validation: Embedded safety and security standards require extensive verification and validation processes to ensure that the systems meet the specified requirements. Requirements management supports the planning and execution of these activities by providing clear and testable requirements, facilitating the identification of suitable verification and validation techniques, and enabling the establishment of traceability between tests and requirements.
- Change Management: Safety and security standards often undergo updates and revisions to address emerging threats and industry advancements. Effective requirements management enables organizations to adapt to these changes by efficiently incorporating new requirements, updating existing requirements, and managing the impact on the development process. It ensures that the safety and security aspects of the embedded systems remain up-to-date and aligned with the evolving standards.
- Documentation and Audibility: Embedded safety and security standards often require comprehensive documentation to demonstrate compliance. Requirements management ensures that all requirements, along with their associated rationale, verification and validation evidence, and change history, are properly documented. This documentation supports audits, assessments, and regulatory compliance, providing evidence of due diligence and adherence to safety and security standards.
In the realm of embedded safety and security standards, effective requirements management is crucial to ensure compliance, mitigate risks, maintain traceability, support verification, and validation, manage changes, and provide auditable documentation. It plays a vital role in developing and maintaining robust, safe, and secure embedded systems.
Requirements Management & Embedded Standards
Requirements management is highly important when it comes to embedded safety and security standards such as ISO 26262 and ISO 61508. Let’s explore the significance of requirements management in each of these standards:
ISO 26262 (Functional Safety for Automotive Systems):
ISO 26262 is an international standard for functional safety in automotive systems. It outlines requirements for ensuring the safety of electrical and electronic systems within vehicles. Here’s why requirements management is crucial in ISO 26262 compliance:
- Capture and management of safety requirements: Requirements management enables the identification, documentation, and management of safety requirements specific to automotive systems. It ensures that safety-related requirements are properly captured, analyzed, and documented to guide the development process.
- Traceability and impact analysis: ISO 26262 requires traceability between safety requirements, system elements, and verification activities. Requirements management facilitates traceability by establishing clear links between safety requirements, design elements, implementation artifacts, and verification results. This traceability enables impact analysis, change management, and effective tracking of safety-related decisions throughout the development lifecycle.
- Risk assessment and mitigation: ISO 26262 mandates the identification, assessment, and mitigation of safety risks in automotive systems. Requirements management supports the analysis of potential risks, their association with safety requirements, and the formulation of appropriate risk mitigation measures. It ensures that safety requirements address identified risks and that their effectiveness is evaluated during the development process.
- Verification and validation planning: Effective requirements management assists in planning verification and validation activities according to ISO 26262 requirements. It helps define the necessary tests, test cases, and acceptance criteria based on safety requirements. By establishing a clear relationship between requirements and verification activities, requirements management ensures that the safety requirements are adequately tested and validated.
- Change management and configuration control: Requirements management plays a critical role in managing changes and maintaining configuration control, which are vital aspects of ISO 26262 compliance. It ensures that changes to safety requirements are properly evaluated, documented, and communicated. Additionally, it helps in maintaining the integrity of the requirements baseline and managing version control throughout the development process.
ISO 61508 (Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems):
ISO 61508 is a standard that addresses functional safety in various industries, including industrial control systems. Here’s why requirements management is essential for ISO 61508 compliance:
- Requirements documentation and management: ISO 61508 emphasizes the need for comprehensive requirements documentation and effective management. Requirements management enables the capture, organization, and maintenance of safety requirements, ensuring that they are well-documented and managed throughout the system development lifecycle.
- Traceability and validation: ISO 61508 requires traceability between safety requirements, design artifacts, and verification activities. Requirements management facilitates the establishment of traceability links, ensuring that each requirement is addressed by appropriate design elements and that the necessary verification activities are planned and executed.
- Risk analysis and risk reduction: ISO 61508 mandates the identification, analysis, and reduction of risks associated with safety-related systems. Requirements management supports the analysis of risks, their association with safety requirements, and the formulation of risk reduction measures. It ensures that safety requirements adequately address identified risks and that their effectiveness is evaluated during the development process.
- Configuration control and change management: Requirements management helps in maintaining configuration control and managing changes, which are essential for ISO 61508 compliance. It ensures that changes to safety requirements are properly evaluated, documented, and controlled. This ensures that the safety requirements baseline is preserved and that any changes are appropriately managed and communicated.
- Verification and validation planning: Effective requirements management assists in planning verification and validation activities based on the safety requirements specified in ISO 61508. It helps define the necessary tests, test cases, and acceptance criteria derived from the safety requirements. By establishing a clear relationship between requirements and verification activities, requirements management ensures that the safety requirements are thoroughly tested and validated, in line with ISO 61508 requirements.
- Safety case development: ISO 61508 emphasizes the development of a safety case, which is a structured argument supported by evidence, demonstrating that the safety requirements have been adequately addressed. Requirements management plays a crucial role in providing the necessary documentation, traceability, and evidence to support the safety case development, ensuring that it aligns with the requirements and objectives specified by the standard.
- Auditing and compliance: ISO 61508 requires organizations to demonstrate compliance with the standard’s requirements. Effective requirements management ensures that safety requirements are well-documented, properly managed, and traceable throughout the development process. This documentation and traceability provide auditable evidence of compliance, supporting external audits and assessments.
Requirements Management & Avionics Standards
Requirements management plays a critical role in complying with avionics standards such as ARP 4754 and DO-178. Let’s explore the importance of requirements management in each of these standards:
ARP 4754 (Guidelines for Development of Civil Aircraft and Systems):
ARP 4754 provides guidance for the development of civil aircraft and systems, including requirements for safety assessment and certification. Here’s how requirements management is essential for ARP 4754 compliance:
- Requirements capture and traceability: Effective requirements management ensures that all applicable requirements, including functional, performance, and safety requirements, are captured, documented, and properly linked to the corresponding design elements and verification activities. This traceability allows for a clear understanding of how each requirement is satisfied throughout the development process.
- Safety assessment and analysis: ARP 4754 mandates the identification and analysis of potential hazards and the development of safety requirements to mitigate those hazards. Requirements management facilitates the analysis of safety-related requirements, their association with identified hazards, and the formulation of appropriate safety measures. It helps ensure that safety requirements adequately address the identified hazards and that their effectiveness is evaluated during the safety assessment.
- Change management and configuration control: Requirements management supports the management of changes to requirements, which is crucial in ARP 4754 compliance. It enables the evaluation, documentation, and control of changes to ensure that safety-critical requirements and associated design elements are properly managed. Configuration control ensures that the requirements baseline is maintained throughout the development process, enabling traceability and preserving the integrity of the system design.
- Verification and validation planning: Effective requirements management assists in planning verification and validation activities according to ARP 4754 requirements. It helps define the necessary tests, test cases, and acceptance criteria based on the requirements. By establishing traceability between requirements and verification activities, requirements management ensures that all requirements are adequately tested and validated, supporting the overall safety and certification objectives.
- Certification documentation: ARP 4754 requires comprehensive documentation to support the certification process. Requirements management ensures that all requirements, along with their associated rationale, verification evidence, and change history, are properly documented. This documentation provides auditable evidence of compliance, facilitating the certification process and regulatory reviews.
DO-178 (Software Considerations in Airborne Systems and Equipment Certification):
DO-178 is a standard that provides guidance for the development of airborne software. It focuses on the software aspects of avionics systems. Here’s why requirements management is crucial for DO-178 compliance:
- Requirements analysis and allocation: Requirements management facilitates the analysis and allocation of high-level system requirements to software requirements. It ensures that software requirements are properly derived, captured, and documented, aligning with the overall system objectives.
- Traceability and impact analysis: DO-178 requires traceability between software requirements, design artifacts, verification activities, and test cases. Requirements management enables the establishment of traceability links, ensuring that each software requirement is addressed by appropriate design elements and that the necessary verification activities are planned and executed. This traceability enables impact analysis, change management, and effective tracking of software-related decisions.
- Change management and configuration control: Requirements management helps in managing changes to software requirements. It ensures that changes are properly evaluated, documented, and communicated and that their impact on the software design and verification is effectively managed. Configuration control ensures that the software requirements baseline is maintained, supporting traceability and preserving the integrity of the software throughout the development process.
- Verification and validation planning: Effective requirements management assists in planning verification and validation activities based on the software requirements specified in DO-178. It helps define the necessary tests, test cases, and acceptance criteria derived from the software requirements. By establishing traceability between requirements and verification activities, requirements management ensures that the software requirements are thoroughly tested and validated, in accordance with the DO-178 requirements. It supports the development of a comprehensive verification and validation plan that addresses all software requirements.
- Requirements-based testing: DO-178 emphasizes the importance of requirements-based testing, where each requirement is traced to one or more test cases. Requirements management enables the establishment of traceability links between software requirements and corresponding test cases. This ensures that all requirements are properly tested, and the test coverage aligns with the specified software requirements.
- Certification documentation: DO-178 requires extensive documentation to support the software certification process. Requirements management ensures that all software requirements, along with their associated rationale, verification evidence, and change history, are properly documented. This documentation provides auditable evidence of compliance and supports the certification activities, such as audits and reviews.
- Tool qualification: DO-178 also addresses the qualification of tools used in the development process. Requirements management plays a role in tool qualification by ensuring that the tools used for requirements management and traceability meet the appropriate tool qualification objectives defined by DO-178. This includes verifying that the tools accurately capture, manage, and trace requirements throughout the development lifecycle.
Relative Cost Of Fixing An Error In Requirements
The cost of fixing an error in requirements can vary depending on various factors. Here are some factors that can influence the relative cost:
- Stage of the project: The cost of fixing a requirements error can be significantly lower if the error is identified and corrected early in the project lifecycle, such as during the requirements gathering and analysis phase. On the other hand, if the error is discovered during later stages of development or after the product has been implemented, the cost of rectifying it can be much higher, as it may require rework, design changes, or even product recalls.
- Magnitude of the error: The severity and impact of the requirements error also affect the cost of fixing it. Minor errors or inconsistencies may be relatively easy and inexpensive to rectify, while major errors that affect critical functionalities or safety requirements can be significantly costlier to address.
- Impact on downstream activities: Requirements errors can have a ripple effect on subsequent development activities. If the error propagates through the design, coding, and testing phases, it can result in significant rework and delays, leading to increased costs. Additionally, if the error goes unnoticed until later stages of the project, it may require modifications to existing components, interfaces, or system architecture, further driving up the cost of correction.
- Discovery and correction process: The cost of fixing a requirements error depends on the efficiency and effectiveness of the discovery and correction process. If the error is identified through thorough reviews, inspections, or validation activities, it can be addressed earlier, reducing the cost. Conversely, if the error remains undetected until it causes issues in the field, the cost of addressing it can be much higher, potentially involving customer support, product recalls, or legal ramifications.
- Organizational processes and culture: The maturity of an organization’s requirements management processes and its culture around quality and error prevention also play a role. Organizations with robust requirements management practices, including peer reviews, quality gates, and traceability, are more likely to catch and rectify errors early, minimizing the associated costs.
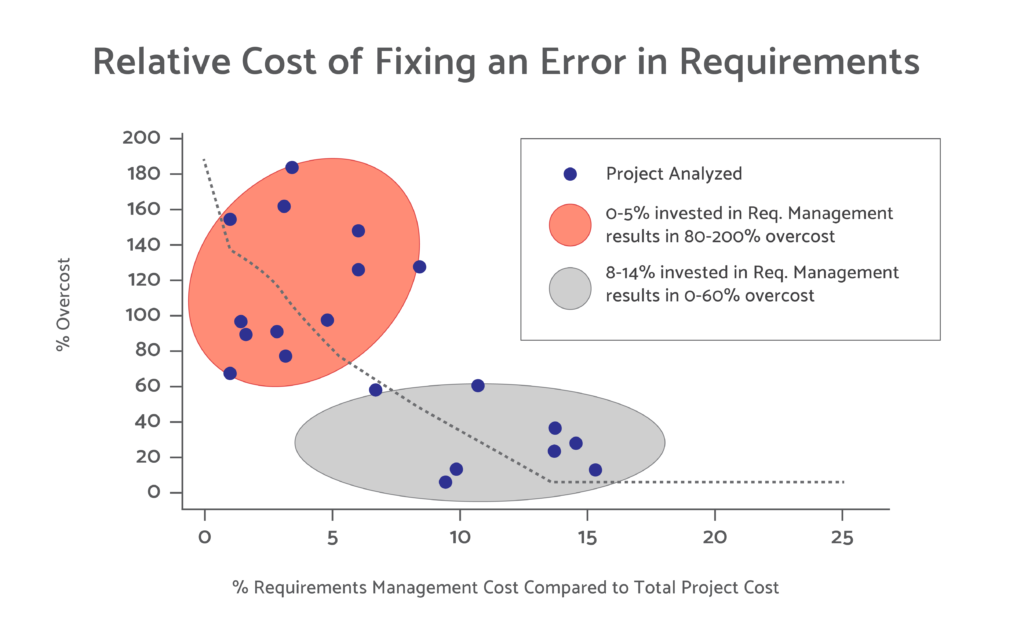
It is worth noting that preventing requirements errors in the first place through effective requirements management, stakeholder engagement, and validation activities is typically more cost-effective than fixing errors after they have propagated into subsequent stages of development or production. Investing in thorough requirements analysis, reviews, and verification processes can help identify and address errors early, reducing the overall cost and impact on the project.
Embedded Safety and Security Standards
Embedded safety and security standards play a crucial role in ensuring the reliable and secure operation of embedded systems. These standards provide guidelines and requirements for the development, implementation, and validation of safety-critical and secure embedded systems. By adhering to these standards, organizations can mitigate risks, enhance system safety, and protect against security threats. Let’s explore embedded safety and security standards in more detail:
Embedded Safety Standards
Embedded safety standards play a crucial role in ensuring the safe operation of embedded systems in various industries. Here are some key embedded safety standards in different domains:

Aerospace (ECSS):
ECSS (European Cooperation for Space Standardization) standards are widely used in the aerospace industry. They cover various aspects of safety and reliability for space systems. For example, ECSS-Q-ST-30C focuses on the management of safety and product assurance, while ECSS-E-ST-40C addresses the requirements for system engineering.
Avionics (DO-178C, DO-254, DO-278, DO-160):
Avionics standards are critical for the development of safety-critical software and hardware in the aviation industry.
- DO-178C (Software Considerations in Airborne Systems and Equipment Certification) provides guidelines for the development of airborne software, including the verification and validation processes.
- DO-254 (Design Assurance Guidance for Airborne Electronic Hardware) focuses on the development and certification of airborne electronic hardware, including integrated circuits, FPGAs, and other electronic components.
- DO-278 (Software Integrity Assurance) addresses the software aspects of air traffic management systems, including requirements for software development and verification.
- DO-160 (Environmental Conditions and Test Procedures for Airborne Equipment) specifies the environmental testing requirements for airborne equipment, ensuring their robustness against environmental factors.
Automotive (ISO 26262):
ISO 26262 is a widely recognized standard for functional safety in the automotive industry. It provides guidelines for the development of safety-related electrical and electronic systems in vehicles. ISO 26262 covers the entire automotive development lifecycle, including hazard analysis, risk assessment, and safety requirements.
Industrial Automation (IEC 61508):
IEC 61508 is a general standard for functional safety in electrical, electronic, and programmable electronic systems in various industries, including industrial automation. It provides a framework for managing functional safety across the entire lifecycle of a system, including hazard identification, risk assessment, and safety integrity levels (SIL).
Medical Devices (IEC 13485, IEC 60601-1, IEC 62304/82304):
Medical devices require compliance with specific safety standards to ensure patient safety and regulatory compliance.
- IEC 13485 is a standard for the quality management system of medical devices. It provides guidelines for the design, development, production, and post-production of medical devices.
- IEC 60601-1 is a standard for the safety and essential performance of medical electrical equipment. It addresses electrical and mechanical safety requirements for medical devices.
- IEC 62304 and IEC 82304 are standards specifically focused on software in medical devices. They provide guidance for the software lifecycle processes, including requirements, design, implementation, testing, and maintenance.
Railways (EN 50126/8/9, EN 50657):
Railway systems require adherence to safety standards specific to the industry.
- EN 50126, EN 50128, and EN 50129 form a set of standards for the railway sector. EN 50126 covers the overall system lifecycle, EN 50128 focuses on software, and EN 50129 addresses the safety requirements for signaling systems.
- EN 50657 provides guidelines for the functional safety of electrical and electronic systems used in railway applications.
These standards help ensure the safety and reliability of embedded systems in their respective industries, providing guidelines and requirements for development, validation, and certification processes. Compliance with these standards is essential for meeting industry-specific safety requirements and ensuring the safe operation of embedded systems.
Embedded Security Standards:
Embedded security standards play a critical role in ensuring the security and resilience of embedded systems against potential threats and vulnerabilities. These standards provide guidelines and best practices for implementing robust security measures throughout the development, deployment, and maintenance of embedded systems. Let’s explore some key embedded security standards in different domains:
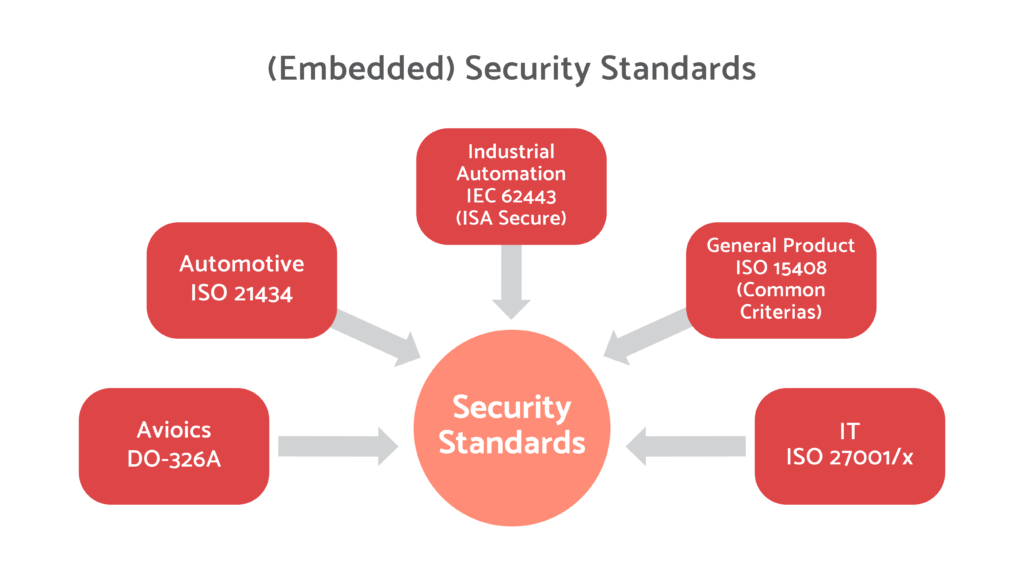
Avionics (DO-326A):
DO-326A is a standard that focuses on the security aspects of airworthiness for aircraft systems and components. It provides guidance for developing a security program, conducting security assessments, and implementing security controls in avionics systems. DO-326A complements safety-related standards such as DO-178C and DO-254 in the aviation industry.
Automotive (ISO-21434):
ISO-21434 is a recently released standard that addresses cybersecurity in the automotive industry. It provides guidelines and requirements for implementing cybersecurity processes throughout the automotive product lifecycle, including risk assessment, threat analysis, security requirements, and validation. ISO-21434 aims to enhance the resilience of automotive systems against cyber threats and protect the integrity and safety of vehicles.
Industrial Automation (IEC-62443 – ISA Secure):
IEC-62443, also known as ISA Secure, is a comprehensive series of standards specifically developed for industrial automation and control systems (IACS) security. It covers various aspects of IACS security, including network architecture, security management, system hardening, secure coding practices, and incident response. IEC-62443 provides a systematic approach to protecting industrial systems from cyber threats and ensuring their availability, integrity, and confidentiality.
General Product (ISO-15408 – Common Criteria):
ISO-15408, also known as Common Criteria (CC), is an international standard for evaluating and certifying the security of information technology products, including embedded systems. It provides a framework for assessing the security features and functions of products based on predefined security requirements. Common Criteria allow organizations to evaluate and compare the security capabilities of different products, ensuring they meet specific security objectives.
IT (ISO-27001/x):
ISO-27001 is a widely adopted standard for information security management systems (ISMS). Although not specific to embedded systems, it provides a comprehensive framework for managing security risks in organizations, including the protection of embedded systems. ISO-27001 includes a set of controls and best practices for implementing an effective information security management system.
ISO-27001 is accompanied by other standards in the ISO/IEC 27000 series, such as ISO-27002, which provides guidelines for implementing specific security controls. These standards can be leveraged in the development and deployment of secure embedded systems.
These embedded security standards play a vital role in guiding organizations in the implementation of security measures, risk assessments, and controls to protect embedded systems from potential threats. Compliance with these standards helps ensure the confidentiality, integrity, and availability of embedded systems, protecting them against security breaches and unauthorized access.
Cybersecurity for Avionics and Automotive, Risk Analysis and Traceability
Cybersecurity for Avionics and Automotive:
Cybersecurity is of utmost importance in the avionics and automotive industries due to the increasing complexity and connectivity of embedded systems. Avionics and automotive systems are becoming more interconnected, integrating features like wireless communication, infotainment systems, and advanced driver assistance systems (ADAS). This connectivity exposes these systems to potential cybersecurity threats, including unauthorized access, data breaches, and malicious attacks.
To address cybersecurity in avionics and automotive systems, industry-specific standards and frameworks have been developed, such as DO-326A for avionics and ISO-21434 for automotive. These standards provide guidance on conducting risk assessments, defining security requirements, implementing security controls, and establishing processes for the secure development and maintenance of embedded systems.
Risk Analysis:
Risk analysis is a fundamental aspect of cybersecurity. It involves identifying potential risks and vulnerabilities, assessing their likelihood and impact, and prioritizing them for mitigation. In the context of avionics and automotive systems, risk analysis helps identify the potential cybersecurity threats and their potential impact on system safety, functionality, and user privacy.
The risk analysis process typically involves the following steps:
- Threat Identification: Identifying potential threats and vulnerabilities that can be exploited to compromise the security of the system. This includes considering both internal and external threats, such as malicious attacks, software vulnerabilities, and physical tampering.
- Vulnerability Assessment: Assessing the system’s vulnerabilities and weaknesses that could be exploited by identified threats. This involves evaluating the security posture of the system, including software, hardware, network, and communication interfaces.
- Likelihood Assessment: Assessing the likelihood of each identified threat occurrence. This involves considering factors such as the system’s exposure to potential threats, the sophistication of potential attackers, and historical data or trends.
- Impact Analysis: Analyzing the potential consequences and impact of successful attacks or security breaches on the system, including safety risks, financial losses, reputational damage, and user privacy concerns.
- Risk Prioritization: Prioritizing risks based on their likelihood and impact to determine the critical areas that require immediate attention and mitigation efforts.
Traceability:
Traceability is essential in ensuring the security and integrity of avionics and automotive systems. It refers to the ability to track and document the relationships and dependencies between various system elements, including requirements, design artifacts, implementation code, and test cases. Traceability provides a transparent view of how security requirements are implemented throughout the system development lifecycle.
In the context of cybersecurity, traceability helps in:
- Requirements Traceability: Linking security requirements to higher-level system requirements and design specifications to ensure that the security measures are properly defined and implemented.
- Design Traceability: Tracing the security features and controls from the design phase to the implementation stage, ensuring that the system is built in compliance with the defined security requirements.
- Testing Traceability: Establishing traceability between security test cases and the corresponding security requirements and design elements to verify the effectiveness of security controls and ensure comprehensive testing coverage.
Traceability aids in identifying potential gaps, inconsistencies, or missing security measures during the system development process. It also facilitates audits, vulnerability assessments, and future system updates or modifications by providing a clear understanding of the security measures implemented.
Defining Cybersecurity Requirements
DO-326A
DO-326A, the “Airworthiness Security Process Specification,” provides guidance for addressing cybersecurity in avionics systems. While DO-326A focuses primarily on the airworthiness aspect, it does provide guidance on defining cybersecurity requirements for avionics systems. The standard emphasizes the importance of conducting risk assessments, identifying security objectives, and developing a security plan that includes specific security requirements.
The main objective of DO-326A is to ensure the security of aircraft systems against cyber threats. It recognizes that aviation systems are increasingly interconnected and susceptible to cyber attacks, which can compromise the safety, integrity, and availability of the aircraft.
DO-326A suggests the following considerations when defining cybersecurity requirements:
- Identifying critical assets and system components that need protection against cybersecurity threats.
- Establishing security objectives and risk tolerance levels.
- Defining security requirements related to secure communication, access controls, software security, and secure development practices.
- Incorporating security controls that address specific risks identified during the risk assessment process.
- Ensuring the compatibility and interoperability of cybersecurity measures with existing systems and aircraft architectures.
- Providing traceability between cybersecurity requirements and other system artifacts.
DO-326A highlights the importance of tailoring cybersecurity requirements based on the system’s characteristics, operational context, and potential threats. It encourages organizations to adopt a systematic approach to defining and implementing cybersecurity requirements, aligning with other relevant standards and best practices.
ISO 21434
ISO 21434 is an international standard titled “Road vehicles — Cybersecurity engineering.” It provides guidelines and requirements for managing cybersecurity risks in the automotive industry. The standard aims to ensure the security and resilience of automotive systems against cyber threats throughout their lifecycle.
ISO 21434 recognizes the increasing connectivity and complexity of automotive systems, including advanced driver assistance systems (ADAS), infotainment systems, and vehicle-to-vehicle communication. These advancements bring about new cybersecurity challenges and risks that need to be addressed to safeguard the integrity, safety, and privacy of vehicles and their occupants.
When it comes to defining cybersecurity requirements, ISO 21434 offers valuable guidance and considerations:
- Risk Assessment: ISO 21434 emphasizes conducting a comprehensive risk assessment to identify potential cybersecurity threats and vulnerabilities specific to automotive systems. This includes considering potential impacts on safety, privacy, and system functionality.
- Security Objectives: The standard emphasizes defining clear and measurable security objectives based on the identified risks and the organization’s risk tolerance. These objectives should align with the desired level of protection and the specific requirements of the automotive system.
- Security Requirements: ISO 21434 guides organizations in defining specific security requirements for automotive systems. These requirements cover various aspects such as secure communication protocols, secure software development practices, access control mechanisms, cryptography, intrusion detection, and incident response.
- Security by Design: ISO 21434 promotes the integration of security considerations throughout the entire development lifecycle, following a “security by design” approach. This includes considering security aspects during system architecture, component selection, development processes, and interfaces.
- Compliance and Auditing: ISO 21434 emphasizes the importance of compliance with relevant regulations and standards. It encourages organizations to define cybersecurity requirements that align with industry-specific standards and best practices. The standard also highlights the need for auditing and verification processes to ensure compliance with defined requirements.
- Collaboration and Information Sharing: ISO 21434 encourages collaboration and information sharing between stakeholders involved in the development, manufacturing, and maintenance of automotive systems. This promotes a holistic approach to cybersecurity and allows for the exchange of knowledge and best practices.
By following the guidance provided by ISO 21434, organizations in the automotive industry can define robust cybersecurity requirements that address the unique challenges and risks associated with automotive systems. These requirements serve as a foundation for designing, implementing, and verifying the effectiveness of cybersecurity measures in automotive systems, helping to enhance the overall security posture and resilience of the vehicles.
Visure Requirements ALM Platform
With its sophisticated tools, Visure Solutions enables companies to develop better products/services quickly while maintaining control and staying compliant with all regulations. It also helps organizations reduce time-to-market, improve quality standards, increase operational efficiency, and accelerate time-to-market effectively. Additionally, it offers a range of sector-specific solutions for industries such as automotive, aerospace and defense, telecoms and electronics, medical technology, energy and utilities, and finance. This makes it easy for businesses to access the expertise they need without having to invest in additional resources or training staff. Visure Solutions is the perfect tool to help businesses get the most out of their product and service delivery lifecycle.
Visure’s Automated Checklist makes it easy to manage compliance without all the manual hassle keep track of everything, so you can focus on what’s important. This way, you can base your design and improvement of your review process around these checklists, which are known to be more reliable.
In other words, by using our product, you’ll be able to increase productivity and alignment among team members. This is done through features such as end-to-end traceability, reusing requirements for different projects, and measuring the quality of requirements with AI – all automatically.
At Visure, we also understand how difficult it is for energy technological organizations to keep up with the digital age while also using legacy tools. That’s why we’ve made it a priority of ours to include easy-to-import and export features from legacy tools such as IBM DOORs as well as a simple migration feature.
Furthermore, with Visure you can utilize the best import and export features from MS Office Word & Excel. You can also promote collaboration across the supply chain by using ReqIF for Data Exchange- an international standard.
By accessing these features and integrations with top-tier industry solutions, you can save time by avoiding the need to manually rework requirements through multiple roundtrip interactions. This process is lossless and duplicates free. With our platform, you can verify that all requirements are met, no matter where they come from.
Visure also helps in simplifying the process of building complex and high-quality products in the Oil and Gas Industry with verified and validated requirements to help you comply with applicable regulatory requirements by combining risk analysis and requirements management in a single solution.
Utilizing Failure Mode and Effects Analysis (FMEA) allows you to precisely estimate the risk associated with FMEA metrics. Once you identify the risks with your risk analysis tools, you can import the results into Visure and link high-risk requirements to those onwards.
This platform helps organizations save time and money, while also ensuring their projects comply with industry standards. It provides a comprehensive suite of features that empower teams to quickly trace and monitor changes throughout the development process. Additionally, it helps ensure compliance with regulatory bodies and standards, allowing oil and gas companies to stay competitive in today’s market. Visure Requirements ALM Platform is an invaluable tool for any organization looking to streamline processes and ensure all project requirements are met.